Meet Recon, Your Web3 Security Guardian
The easiest way to set up and secure your Web3 applications using Invariant Testing
In our continuous pursuit of Web3 security excellence, we are excited to announce our partnership with Recon, a cutting-edge platform that streamlines invariant testing for Solidity smart contracts.
Invariant testing is a powerful technique that helps identify vulnerabilities and potential exploits by systematically checking if certain properties (invariants) hold across various code paths and inputs.
Let’s understand how Recon helps you write and run invariant tests:
Introducing Recon
It offers a free Invariant Test Scaffolding Tool to help developers build their invariant tests quickly.
They also offer a paid service to run invariant tests in the cloud, which is called Recon Pro.
They’ve been helping projects like eBTC and Centrifuge strengthen their security.
Why
Due to their extensive work, the Recon team has reverse-engineered the vast majority of exploits that have occurred over the past few years. This first-hand experience provides them with invaluable insights into the root causes of these incidents and the need for more robust security measures.
Below we hear from Alex, who recounts two personal stories about projects that fell victim to exploits, shedding light on the circumstances that ultimately led to the creation of Recon.
ELASTIC SWAP
Back in 2022, donation attacks were somewhat of a novel vector.
The Elasticswap codebase was reviewed by Code4rena, an organization they’ve been working with since 2021.

An attacker found out that by donating some tokens, they were able to convince the AMM to give away more value than intended, leading to a loss of $850k.
A simple donation attack leads to this.
How is it possible that nobody has tried this?
Was there a way to automate this?
EULER
Euler V1 went through multiple security reviews and brought forth a more mature way to discuss risk when it comes to TWAP oracles, as well as isolated lending.
Many of their colleagues were using Euler, and many of our peers did Security Reviews of Euler either directly or as part of Due diligence for integrations.
Famously, Euler was exploited due to a small change, that was added as an afterthought.
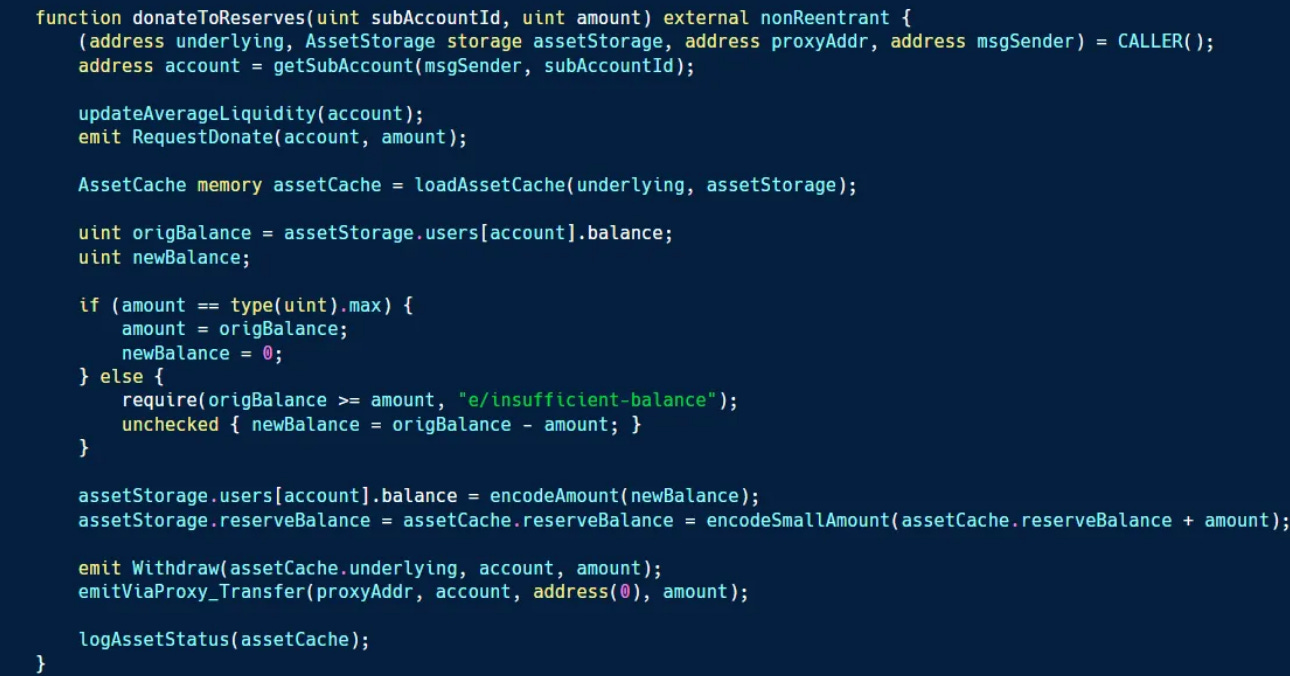
Looking back at the details of the Euler exploit, the Recon team believed and still believes that the main issue was a lack of sufficient coverage.
The review for the crucial change that enabled the exploit was a small, short, solo review, rather than what they refer to as a "Security Contest," where tens or even hundreds of professional white-hat hackers compete to find the most unique bugs.
Not enough scrutiny was given to the change before it was implemented, allowing the vulnerability to slip through. While the exploit appeared highly complex from the outside, the Recon team recognized that it could have been caught with a single global property: "No Direct Action should make an account Liquidatable."
This check would have allowed the fuzzer to do what it does best – try random combinations of transactions and reveal any instances where this property was violated.
It was these two high-profile incidents that motivated the Recon team to take action. Initially, they developed their own code generation tool for Foundry, which would set up automated function calls and then check if an attacker gained value at the end of the sequence.
This was able to find the Elasticswap exploit within a few hours with no adjustments (just brute force) and was able to find the bug within minutes with a small amount of tweaks.
They were never able to reproduce the Euler exploit through this tool; the complexity of generating thousands of lines of poorly optimized boilerplate code was too much for them, given the team had their day job.
A pivotal moment came when the Recon team encountered Antonio's research on Invariant Testing.
Antonio, a security researcher with a development background and passion for open source, had conducted multiple workshops focused on Invariant testing at OpenSense, Spearbit, and the DeFi Security Summit.
Upon studying how Invariant Testing worked, the Recon team realized they had been building a poorly engineered version of Echidna, Trail of Bits' battle-tested open-source Invariant Testing tool.
Fortuitously, Antonio had created Fuzzy,
A cloud-based fuzzer devised a way to make Invariant Testing debuggable within Foundry, offering the best of both worlds: fast detection of broken properties and easy, comfortable debugging.
Inspired by these key ideas,
The Recon team built their platform, which has undergone multiple iterations over the past five months.
They are now excited to share Recon with the community, allowing all open-source Foundry projects to scaffold and run Invariant Tests locally for free through their open-source Create-Chimera-App.
To date, over 150 Solidity developers and security researchers have tried Recon, and the team has executed more than 800 fuzzing jobs on their cloud platform.
The Recon team shares their work with the hope that the community can learn from past mistakes and embrace Invariant Testing to prevent a vast number of exploits.
If you wish to try Recon you can do so at:
If you have specific questions or would like to work with the recon team, you can reach out to Alex on Twitter:
https://twitter.com/GalloDaSballo
Over the next few months, they will continue to work on Recon to help developers write safer code while preventing real-world exploits.











